It’s hard to believe, but based on statistics, about a quarter of Internet users have used a vpn client at least once, which is nearly 1 billion people.
Everyone had a different reason, and not all of them are hackers, or shady characters. Around 80% of all VPN users regularly pay for cognitive and entertainment services such as music, audio books, movies, video games, etc.
But even the most staunch enthusiasts, who are well versed in the properties of VPN, do not always have a complete understanding of all the functionality of the technology.
This is our guide on how VPN works and the most important VPN client features.
What is a VPN
VPN client is a VPN service program installed on your device. Information about what operating systems the vpn client is compatible with can be found on the official website of the chosen service. As a rule, these are the most common operating systems: Windows, macOS, Linux, iOS, Android and others. Installing the vpn client is free, but in most cases, using the service requires a paid subscription.
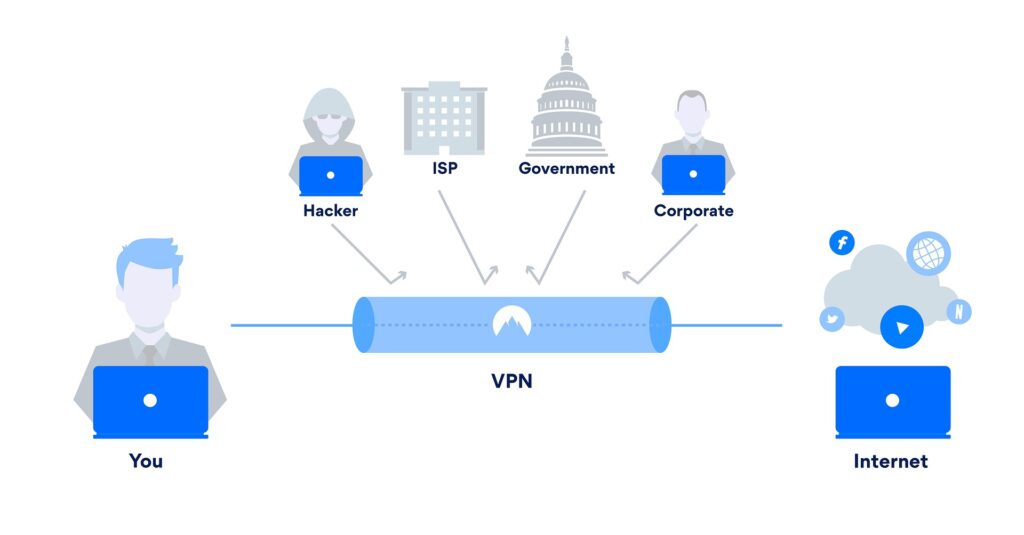
If you’re interested in VPN, you’re probably already familiar with the term. Geolocation is used to control content on the Internet, among other things. For some reason, some sites or streaming videos may not be available in your country. This is possible by blocking ip addresses located outside the country. In conjunction with the rest of the parameters, ip address is one of the components of geolocation.
VPN client features
Access
Today, access to blocked or unavailable content is the driving force behind the sales of WAPs in the individual sector. Among other reasons, streaming multimedia and Internet movie libraries (YouTube, Netflix, Disney etc.), which have gained enormous popularity due to the rapid development of wireless and mobile Internet, are worth mentioning.
You can also use a VPN to access blocked sites. It can be blocked by the sysadmin at work, an institute or a public library, or the domains listed in the registry of banned sites (the analogue of such in your country).
Activity log
A very important indicator of a truly secure VPN is the absence of an activity log. This is a record of all activities performed on the Internet through the VPN connection. That is, where, when, from what device and operating system and what exactly you were browsing online during the time the VPN was activated. If there are no logs, respectively, it becomes impossible to track your actions.
Protection of personal data
It is no secret that all our activities on the Internet are tracked by corporations, for whom we are commodities. Targeted advertising is imposed in this way and our personal data is carefully analyzed, processed and passed on to third parties.
IP address
Every device connected to the Internet has its own unique address. The reason ip addresses exist is the same as your email address – so your device can be found. The IP address tells other computers exactly where your device is located. This information is publicly available, if necessary any user can check the real address of a person by his IP address. One of the key properties of a vpn, is the masking of the ip address.
Cross-platform
Must have feature of VPN is compatibility with any OS and availability on all sorts of devices from cell phones to game consoles. As a rule, one VPN subscription can be used on several devices at once.

Routers
Some VPN services can be set up on your router. This allows you to protect all devices connected to your local WI-FI instead of each one individually. This is a very common and convenient feature, especially for people with a large number of devices connected to the Internet. The only drawback may be the router’s firmware for VPN, but the support service of the purchased service should be able to help.
Unlimited bandwidth
When choosing a VPN, it’s important to understand if your provider has limits on Internet consumption. Almost all free VPN services set a limit, for example, once you have used 500 MB, your subscription is no longer valid until you pay for a paid subscription. Paid VPNs usually provide unlimited use of the service.
Server obfuscation
This term is widespread among VPN providers and its main function is to hide the fact of using VPN. It may sound absurd, but it is also possible to establish the fact of using an VPN. This is what the server obfuscation feature is for, although not many VPNs offer this feature.
Security protocols
This is a set of rules that are used to negotiate the connection between the vpn VPN client and the VPN server. Protocols are an intermediary between your device and the server to which you connect. The more powerful is the protocol, the higher is the level of traffic encryption. At the moment, the most common protocols are PPTP, SSTP, L2TP/IPSec and IKEv2/IPSec. But the most reliable was and remains OpenVPN.
International services
Knowing English is always a plus, but not everyone has the opportunity or desire to learn it. Although modern vpn applications and vpn clients are quite understandable without knowledge of English, international services make using vpn much easier.
Speed
No one wants to face endless buffering, so speed is one of the key indicators of a good VPN service. A VPN slows down your internet connection as it is, neglecting this criterion can play a cruel trick. Especially if you need access to servers located in another part of the world. The fastest VPN services.
Below is an example speedtest of ExpressVPN:
| Server location | Download speed | Upload speeds | Pings |
|---|---|---|---|
| United States | 85.79 Mbps | 68.57 Mbps | 348 ms |
| United Kingdom | 89.12 Mbps | 74.52 Mbps | 131 ms |
| Australia | 86.01 Mbps | 93.87 Mbps | 165 ms |
| Hong Kong | 86.12 Mbps | 93.89 Mbps | 256 ms |
| Singapore | 78.64 Mbps | 93.90 Mbps | 92 ms |
Torrents
Free movies, audio books, music, games – all available for free on torrents. But first, using torrents is illegal, because in 99% of cases the distribution and download is for licensed or copyrighted materials. Secondly, torrents themselves are not safe and are often a breeding ground for malicious files and viruses. We strongly recommend using vpn for torrents.
Vulnerabilities
Once again, there is a threat lurking everywhere on the Internet. It can be a malicious file, surveillance, a virus, and identity theft. Such vulnerabilities are spread to all devices connected to the network. There is no absolute guarantee, even with the strongest vpn-encryption and the best antivirus. But still, a reliable VPN greatly reduces the possibility of hacking or loss of confidential information.
Every provider, and as a rule, they have a corresponding price tag. If you need VPN only for a certain task, it probably makes sense to narrow down the choice of services for this particular need.
Censorship
In many parts of the world the Internet is limited to local sites, social networks and a scant assortment of information resources. Governments thus attempt to control free speech to further their own ends rather than to protect themselves from the potential terrorist threats they so often cite. Internet censorship is a controversial phenomenon, as the Internet was created and is supposed to exist as a global world wide web, but in fact it is just the opposite. VPN allows you to bypass censorship in most countries, except perhaps in China, and that even in the “Celestial Empire” some VPN services is working quite well.
Private DNS
Many VPNs only protect your Internet traffic and leave your DNS queries unprotected and vulnerable. But there are quite a few solutions that solve this problem by using their own private DNS servers on each VPN server.
Having a private DNS server is an additional level of protection and anonymity.
Encryption
Encryption is the process by which data is encrypted so that it remains inaccessible to unauthorized users. This helps protect personal information, sensitive data, and can increase the security of communications between your devices and servers. Most VPN services use two types of 128 MB and 256 MB encryption. The latter is the most secure although it can sometimes have a negative impact on data transfer speeds.
Sending emails through a VPN server is the best way to keep your correspondence anonymous. Some providers offer their own email that you can use for free. Instead of sending emails from your own IP address, a VPN will assign you another, in which case the sender of the email cannot be identified.
Jurisprudence
Assuming one fact that a VPN will protect your online activities from prying eyes is not always true. VPN companies, like any other industry, are still subject to the laws of the country in which they are registered. There are a number of states where access to any servers, including VPN companies located in the country, is regulated by law. Under any pretext, government agencies can always get access to the servers where all your Internet activity is recorded. That is why most premium VPN providers are registered in countries where access to personal information is denied. They are usually from Central America or the Caribbean region.

