VPN protocols are tools used to provide an encrypted connection, hide your IP address. Some may be more private, others may be faster, but experts agree – none of them are perfect. The list of major VPN protocols:
All premium VPN providers automatically connect to the best available VPN protocols. Let’s discuss each of them with their pros, cons and affordability.
1. OpenVPN
Released in 2002, the OpenVPN protocol quickly rose through the ranks and is now ranked number one for security. All premium VPN providers connects with this protocol by default.

OpenVPN protocol comes with two network protocols:
- UDP (User Datagram Protocol)
- TCP (Transmission Control Protocol)
UDP is faster and TCP is more secure and gets through firewalls better.
This protocol has a number of ciphers such as AES (128 and 256 bit), ChaCha20, Blowfish, etc. Simply put, you can think of the different ciphers as different recipes with the ultimate goal of providing a fast encrypted connection.
And if you can try the OpenVPN protocol for free, you can consider yourself technically savvy.
However, there is one drawback that detracts from this otherwise great VPN protocol, and that is its heavy code base. While it provides excellent security, it affects speed.
You can use OpenVPN with well-known VPN providers such as ExpressVPN, SurfShark, NordVPN.
2. WireGuard
WireGuard is another open-source VPN protocol that had its first stable release in 2020. With just over 3,800 lines of code, WireGuard has minimal attack surface and provides excellent encryption speed. It uses ChaCha20 encryption and lacks the options available in the OpenVPN protocol.

On the other hand, WireGuard’s limitations also eliminate the risk of misconfiguration. But for privacy-conscious people, the situation is not very pleasant, at least not out of the box.
By default, WireGuard requires a static IP address, which kills the very reason – the privacy that the VPN is used for. To get around this, VPN providers implement their own versions of WireGuard, such as NordLynx from NordVPN.
Finally, WireGuard may not be as good for circumventing censorship because it does not support TCP.
3. SoftEther
Released in 2014, SoftEther is a free, open-source VPN protocol that provides fast and reliable connections. It appeared as a research thesis at the University of Tsukuba, Japan.

Internal tests by the university claim that it is several times faster than the OpenVPN protocol.
SoftEther supports AES-256-bit encryption among several other strong ciphers. It also uses TCP port 433, which allows it to bypass firewalls well.
A security audit in 2018 found 80 vulnerabilities, but these were fixed in the next update. It’s a robust option that can be used effectively to bypass geo-censorship.
4. IKEv2/IPSec
This pairing is best for getting in and out of multiple networks. In case you’re wondering, IKEv2 stands for Internet Key Exchange version 2 and IPsec is short for Internet Protocol Security.
IKEv2 was developed by Microsoft and Cisco as a joint venture. As a protocol, IKEv2 is responsible for the authenticated VPN tunnel, and IPSec encrypts that connection. Together, IKEv2/IPSec form a great VPN protocol.
This pair supports high security ciphers such as AES, Blowfish, etc. The connection is over UDP ports, so firewalls can be a problem for this VPN protocol, especially in a country like China. And the fact that it’s a closed-source project developed by commercial organizations could be a drawback, according to security advocates.
Finally, rumors that the NSA has compromised IPSec do not go in its favor.
5. L2TP/IPSec
Like its predecessor, Layer 2 Tunneling Protocol (L2TP) uses IPSec, which supports strong ciphers such as AES-256. L2TP/IPsec encrypts your data twice. However, this extra protection affects the speed of the connection, making it slower than its counterparts.
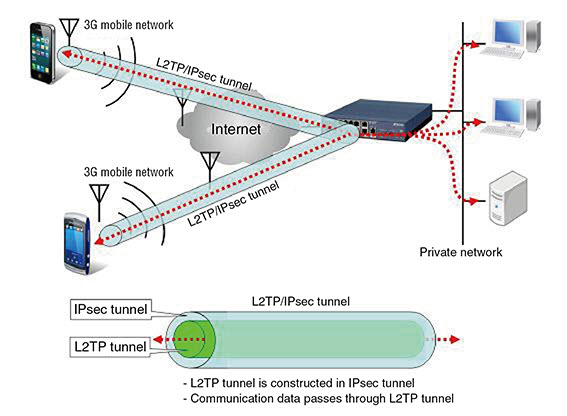
Protocol was developed by Microsoft and Cisco as an improvement to PPTP. It also uses UDP ports, which makes it less attractive to users trying to circumvent censorship.
As a result, it is subject to the same security problems as IKEv2/IPSec.
6. SSTP
Secure Socket Tunneling Protocol (SSTP) is again a Microsoft product. It provides the highest speed and secure connection with AES-256 bit encryption.
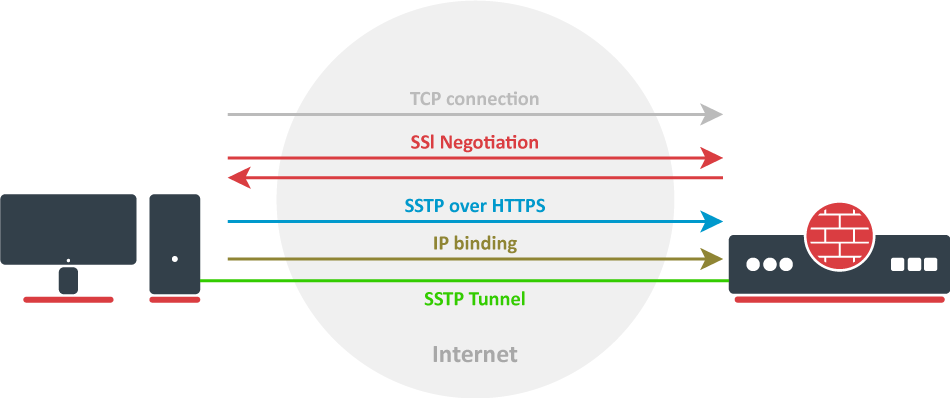
SSTP should be your first option for unblocking geo-restricted content because it works over TCP port 443, the same port used for HTTPS connections. But it is a closed-source project with a questionable legacy from Microsoft.
Therefore, it is not recommended to use it to transfer sensitive data.
7. PPTP
Point-to-Point Tunneling Protocol (PPTP) can be called an outdated VPN protocol that most VPN users tend to avoid. It is very fast, but one of the least secure options on this list. At its best, PPTP can use 128-bit encryption, trading security for speed.
PPTP uses TCP port 1723, which helps bypass censorship. It is also a closed-source protocol from Microsoft, which has reportedly been hacked by the NSA.
In the end, it is the least recommended option if the very purpose of using a VPN is important to you.
8. Proprietary protocols
These are proprietary solutions developed by some VPN providers, such as NordLynx by NordVPN, which is a modified WireGuard. Similarly, there is Catapult Hydra, OpenWeb, CamoVPN, etc. Using these options can be good, especially with a native VPN service.
But open source options that are decades old may be better at protecting user privacy.